Subdomain Takeover Via Flywheel
Flywheel is managed WordPress hosting built for designers and creative agencies to build, scale, and manage hundreds of WordPress sites with ease. One can set up a WordPress site in less than two minutes without any complex configuration.
As described by independent cybersecurity researchers, it is possible to create perform subdomain takeovers using such services, what can be widely used by possible attackers, but also red-team specialists and penetration testers:
https://github.com/EdOverflow/can-i-take-over-xyz/issues/220 https://github.com/EdOverflow/can-i-take-over-xyz/issues/242 https://twitter.com/Itumeleng_Les/status/1454532272271601668
As a result of several recent protests and other research work — I decided to share it with the information security community because such problems exist on many services.
Please, note, that this is not the fault of Flywheel at some point, because they are not a managed DNS service provider.
Same time, several potential improvements could be done in order to prevent an ability to add records with domains to which potential attacker doesn’t have any relation. For example:
- verification via TXT record
- verification via a CNAME record
- validation of domain via e-mail (code to be sent to e-mail visible in WHOIS records)
The owners of the domains may also do a better job in auditing of the used DNS records — one of the main pain points leading to subdomain takeovers.
The Vulnerable Subdomain looks like this:

How To Exploit?
All you need is just a Subscription on Getflywheel the little one that costs 15$ per month.
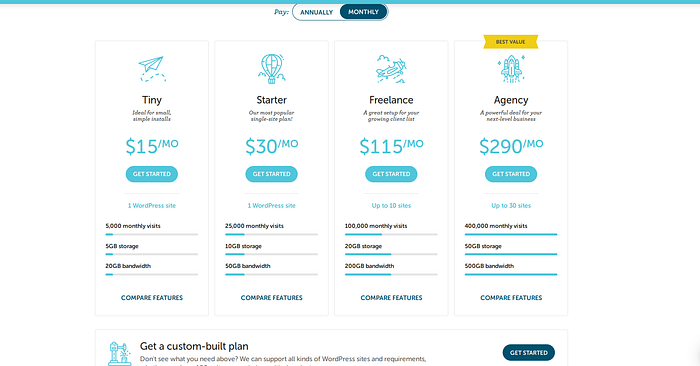
After Registering And payment Process you need to create a site with our subscription We can only create only one site.

After Filling in this Info you this screen will appear

once creating was finishing you will receive an Email.
Now we had created our site we need to connect it with our vulnerable Subdomain.

Now we should press on add domain button like this.


How to find it?
You can find using nuclei tool with this Template.
Severity: High
Impacts: An attacker can use this misconfiguration to takeover the subdomain, publish arbitrary contents, run malicious javascript code at the user’s end, harvest credentials using phishing attack, deface a website, etc also steal the cookies of the user if cookies are scoped to the parent domain and escalate to account takeover.
Remediation: The DNS entry for the subdomain should be removed from DNS records if not in use.
Type of DNS Record is: A Record

I hope this write may help Anyone face this Type of Takeover.
Thank you for reading
wait for the best.
Ahmed Elmalky (Offensive Security Researcher At Resecurity).
